Solve the Complexity of Regulatory Compliance
With 75% of the global population covered by privacy regulations and over 160 laws worldwide, achieving compliance is more challenging than ever. Cross-border privacy laws like the GDPR, DORA, and Québec’s Law 25, for instance, require organizations to navigate regional nuances, while industry-specific mandates like HIPAA and PCI DSS add another layer of complexity.
The stakes are high: organizations face mounting costs, projected to exceed $1.2T globally in 2025, alongside risks of non-compliance, including fines and reputational damage. Compounding the issue, 70% of businesses struggle with secure cross-border data sharing, creating bottlenecks for innovation and operations.
Organizations need a proactive approach—one that embeds compliance into every stage of the data lifecycle, ensuring resilience across a dynamic regulatory landscape.
75%
Global population covered by privacy regulations
160+
Privacy laws enacted worldwide
$1.2T
Projected global compliance costs by 2025
70%
Struggle with cross-border privacy
Compliance Without Compromising Operations
Protect Data While Meeting Regulatory Standards
Security architects must stay ahead of evolving regulations, ensuring sensitive data is protected at all times—whether it’s stored, in transit, or in use. The stakes are high: non-compliance can result in fines, reputational damage, or operational disruptions. Protegrity simplifies compliance with proactive data protection and continuous monitoring. Our platform ensures PII, PHI, and PCI data meet the strictest global standards, giving security architects the tools to secure sensitive data and maintain compliance without adding complexity.
Build Architectures That Align With Compliance
Data architects must design systems that support business goals while adhering to strict regulatory requirements. This means embedding compliance into every layer of the architecture without sacrificing innovation or scalability. Protegrity enables data architects to design systems that make compliance seamless. With automated enforcement policies and robust data classification, our platform empowers architects to meet evolving regulatory mandates while driving innovation and delivering business value.
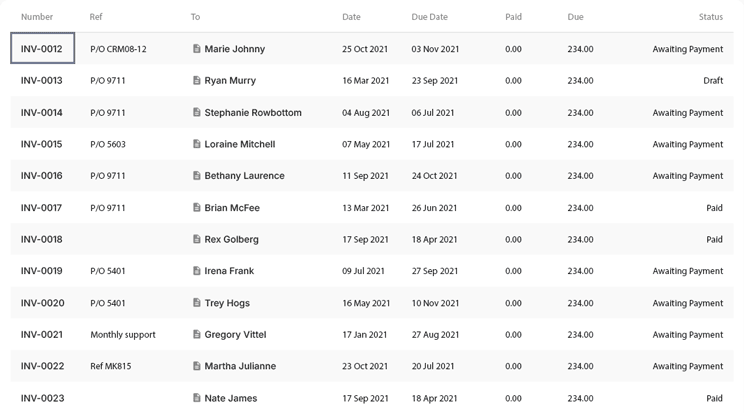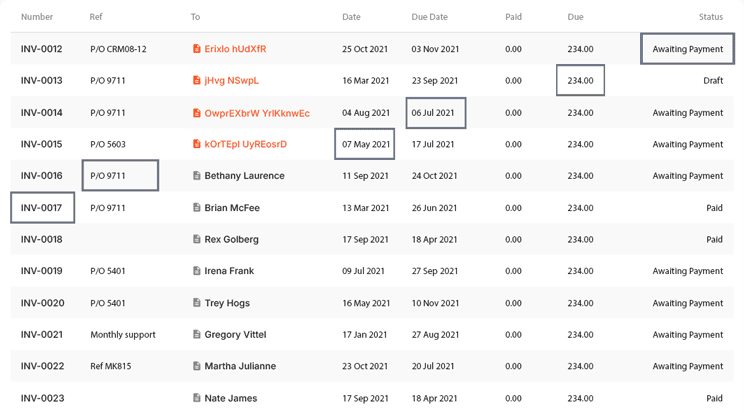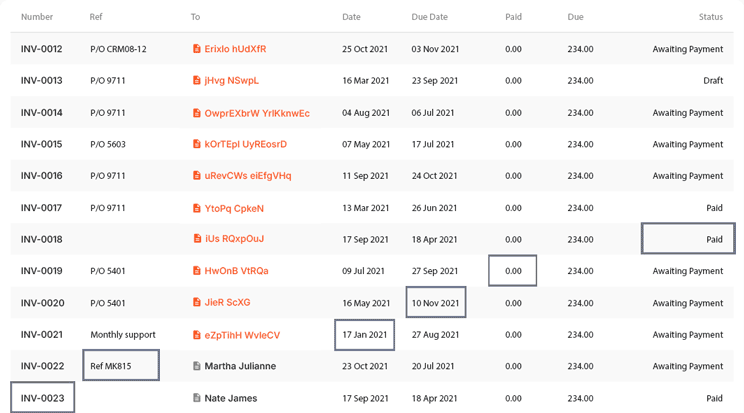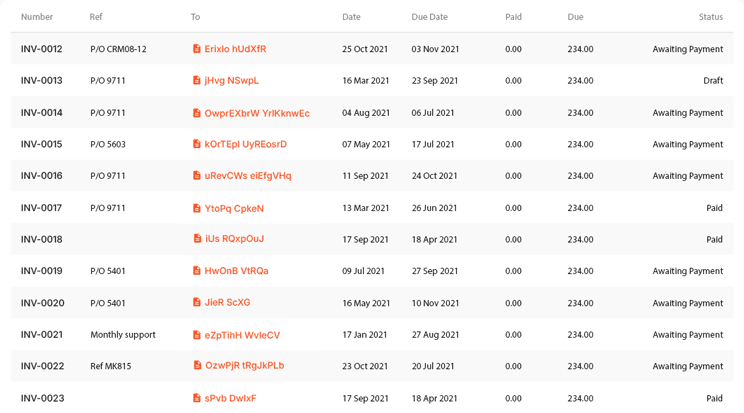
Discover and Identify Sensitive Data
Protegrity’s platform discovers sensitive data, such as PII, PHI, and PCI, across systems, applications, and environments. This discovery process identifies where sensitive information resides and flows, providing critical insights for managing compliance risks and securing data effectively.
Classify and Protect Sensitive Data with Protectors
As sensitive data enters systems, Protegrity’s platform classifies it in real time and applies vaultless tokenization or encryption through its protectors. This ensures that data remains protected throughout its lifecycle while meeting compliance standards like the GDPR, HIPAA, and PCI DSS.
Dynamically Enforce Compliance Policies with ESA
The Enterprise Security Administrator (ESA) enforces compliance policies dynamically across hybrid and multi-cloud environments. Tailored to regional regulations and organizational needs, ESA ensures real-time policy enforcement, enabling organizations to adapt to evolving compliance demands without disrupting operations.
Online Demo
Secure data sharing meets regulatory compliance
Envision your organization’s future with an online or custom live demo.
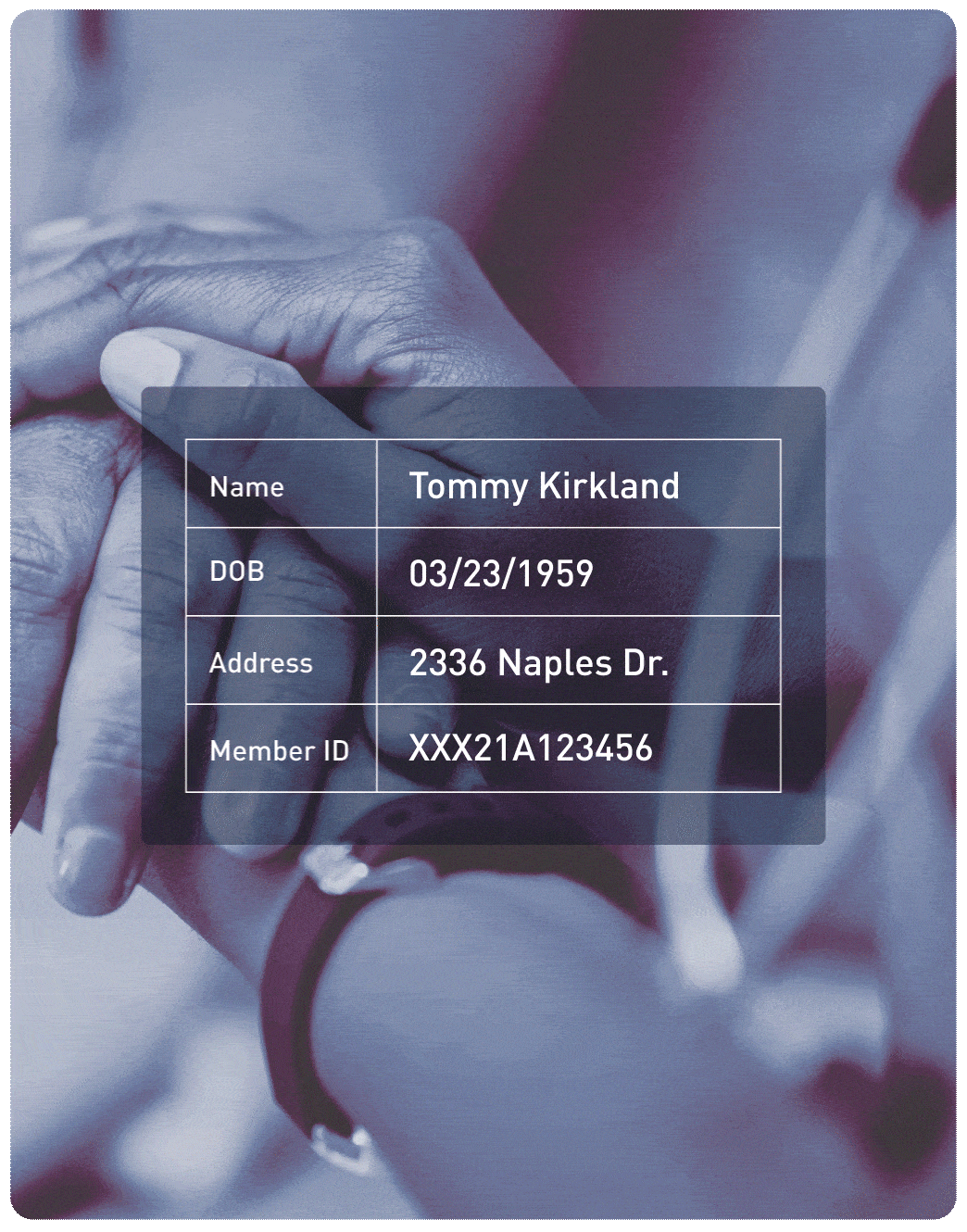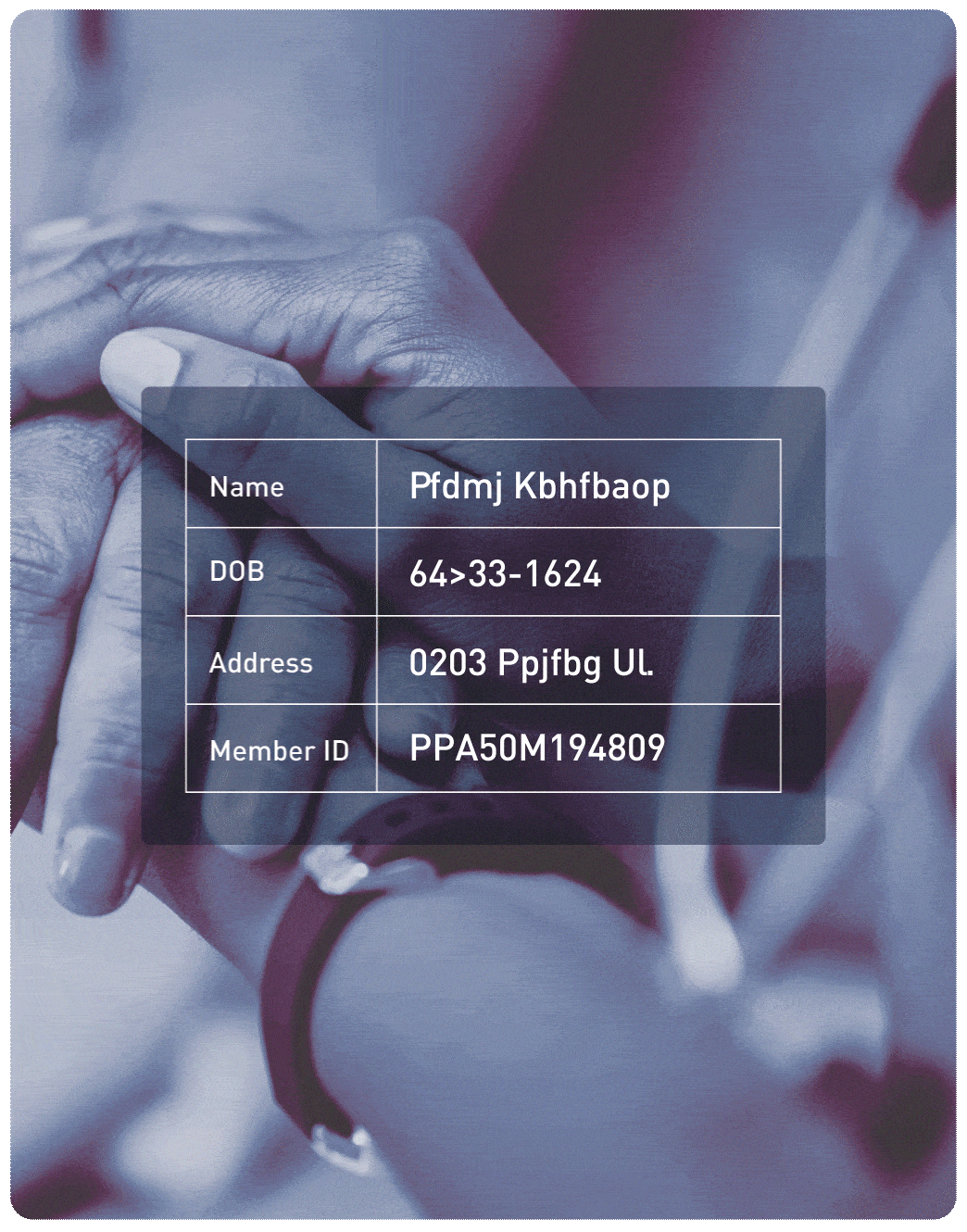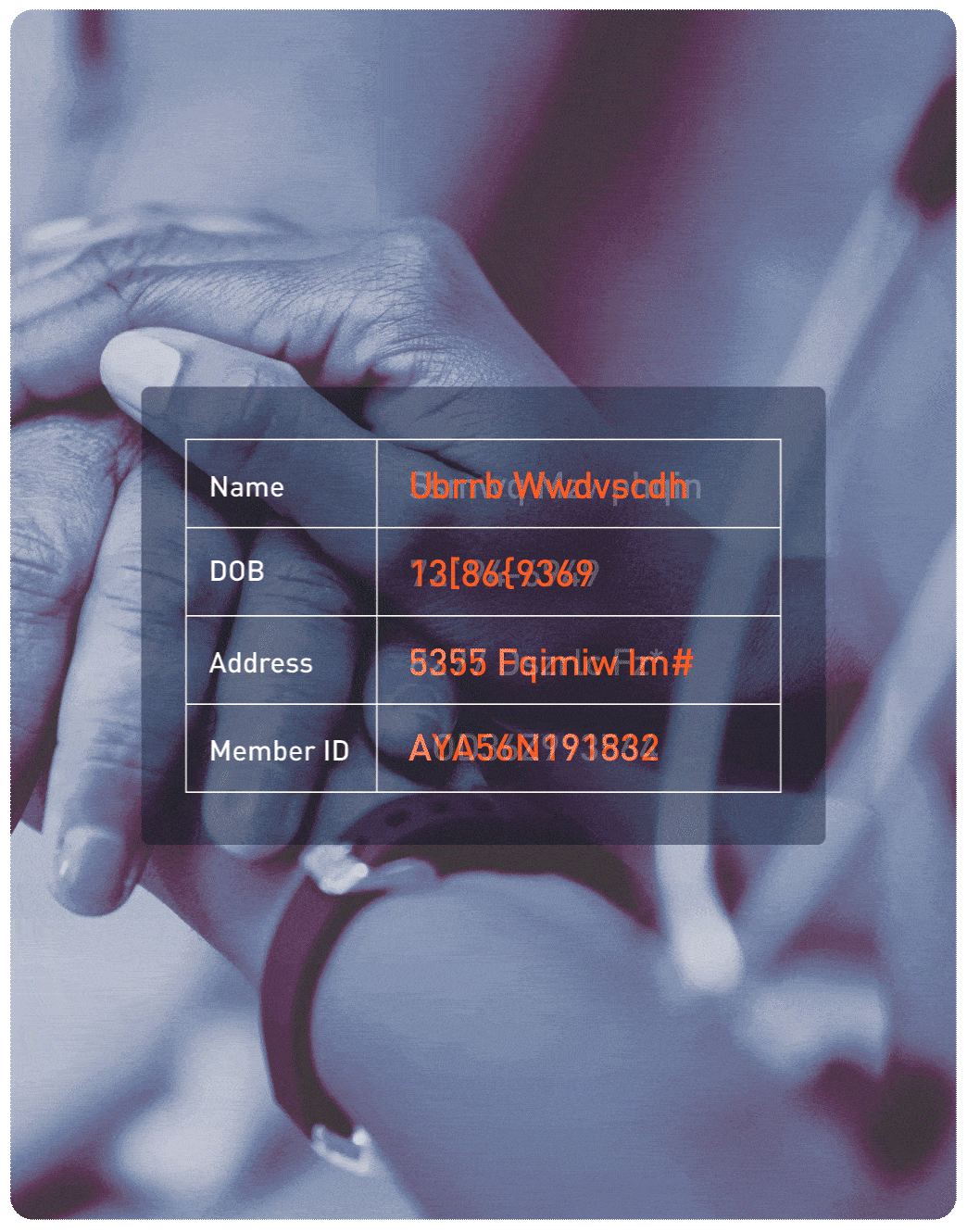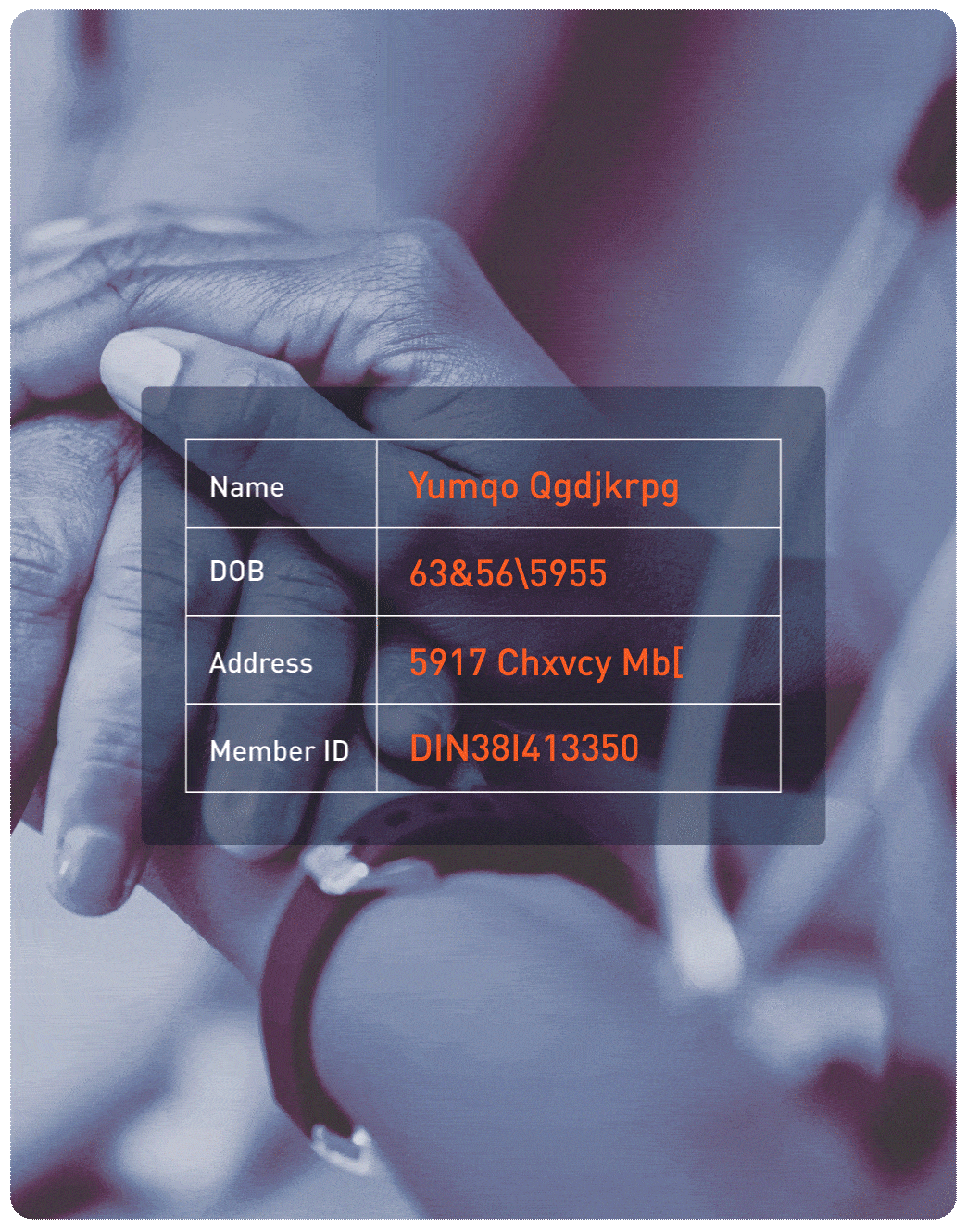

One of the top 5 health insurers needed to meet HIPAA compliance while enabling secure data sharing for claims processing and analytics. Protegrity’s platform applied tokenization and encryption across sensitive health data, ensuring compliance without disrupting operations. The solution supported continuous compliance audits and reduced manual reporting efforts by 40%.
THE PROTEGRITY ADVANTAGE FOR COMPLIANCE
Without Protegrity
- Manual compliance processes: Organizations rely on manual steps to achieve compliance, leading to delays, errors, and increased audit risks.
- Fragmented policies across systems: Inconsistent security and compliance policies increase the risk of gaps and regulatory violations.
- High risk of non-compliance fines: Legacy systems fail to meet evolving regulations, leaving organizations vulnerable to penalties and reputational damage.
- Overwhelming complexity in data classification: Identifying and protecting sensitive data is time-consuming and error-prone, leading to potential breaches.
- Costly and inefficient audits: Manual audits and reporting require significant resources, delaying regulatory certifications and increasing costs.
With Protegrity
- Automated compliance and audit readiness: Protegrity automates compliance through tokenization, encryption, and policy enforcement, ensuring continuous readiness for audits.
- Centralized compliance policy management: Protegrity provides a unified platform to enforce consistent compliance policies across hybrid and multi-cloud environments.
- Future-proof compliance: Protegrity adapts to evolving regulations like the GDPR, HIPAA, and PCI DSS, reducing risks of fines and ensuring organizations stay ahead of compliance requirements.
- Efficient data classification and protection: Protegrity scans, classifies, and protects sensitive data, including PII, PHI, and PCI, reducing operational complexity.
- Streamlined reporting and audit efficiency: Protegrity’s platform generates real-time audit logs and reports, simplifying regulatory audits and reducing compliance costs.
Compliance-Centric Architecture for Sensitive Data Protection
This architecture highlights how sensitive data is secured across its lifecycle to meet regulatory compliance standards such as the GDPR, HIPAA, and PCI DSS. By embedding data security and governance mechanisms at critical touchpoints—ingestion, storage, processing, and consumption—it ensures that sensitive data is protected, monitored, and accessible only to authorized users.
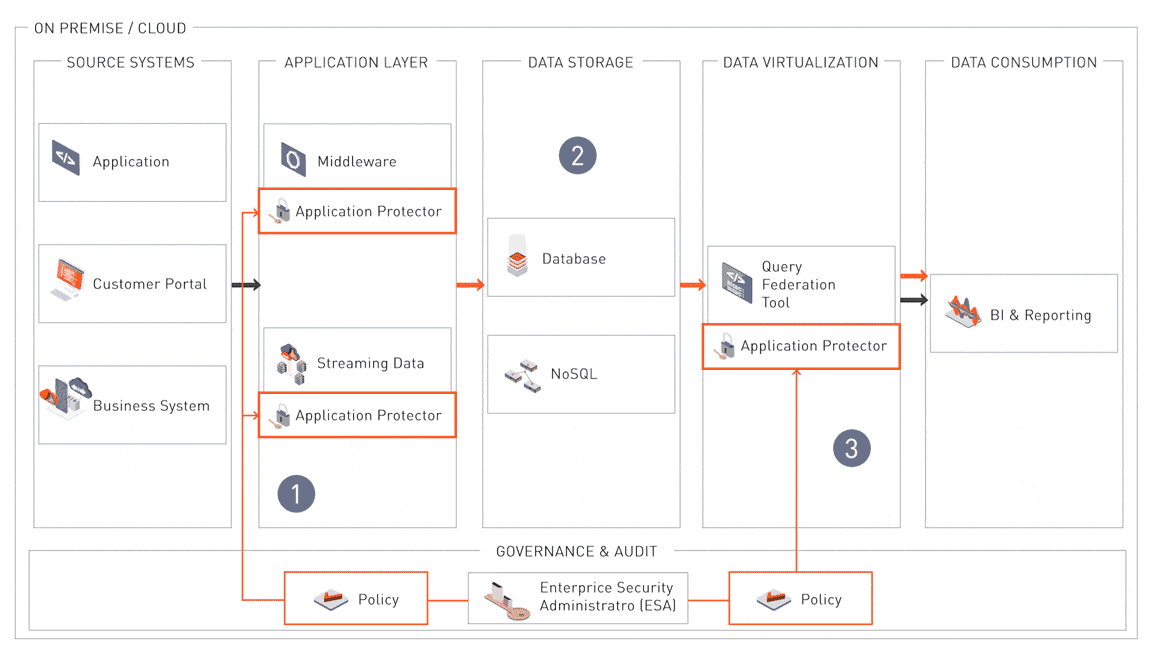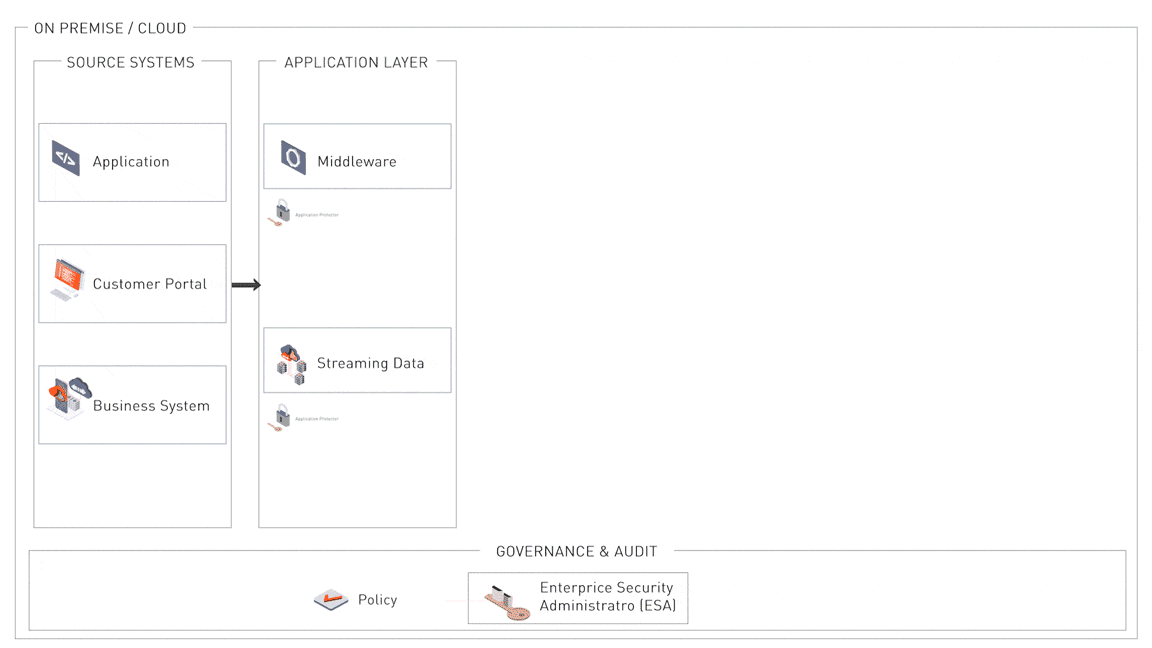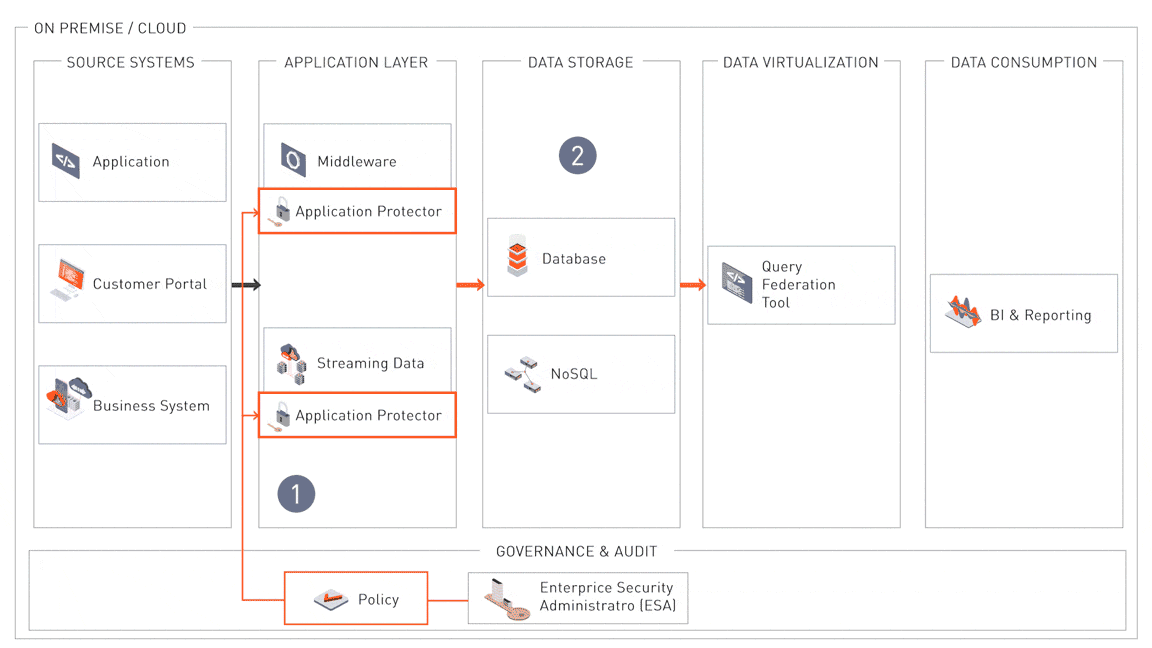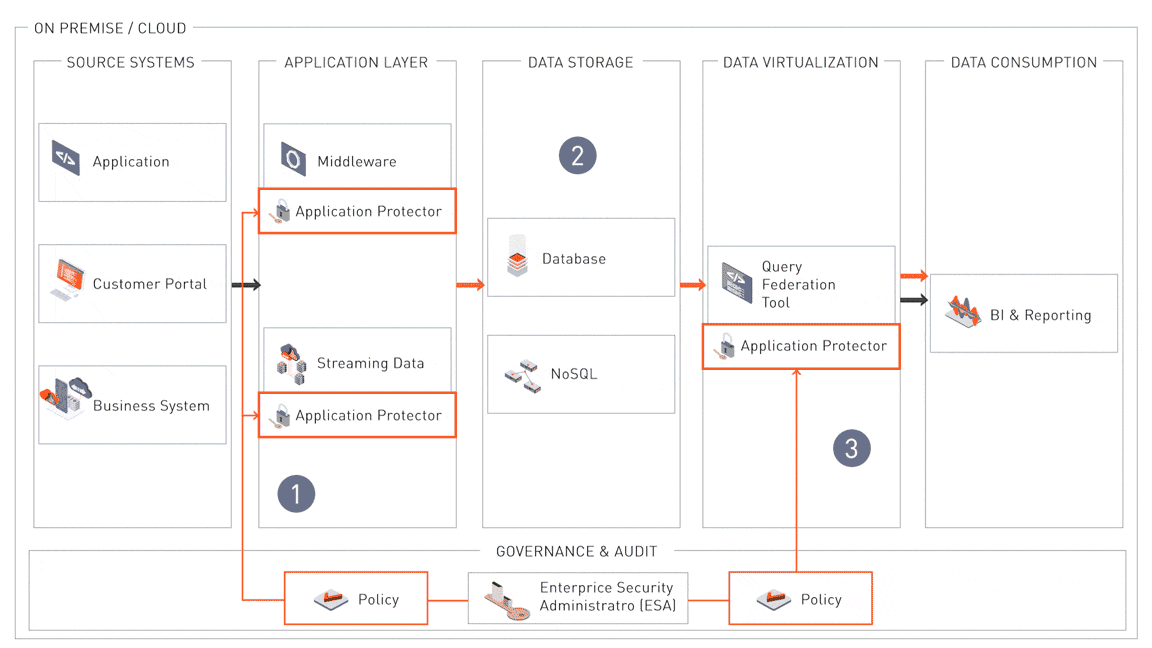
Governance and Audit
At the core of this compliance architecture is the Enterprise Security Administrator (ESA), which provides centralized governance for data security policies. Security administrators can define, deploy, and audit these policies across systems and environments, ensuring consistency and compliance. The ESA integrates seamlessly with frameworks such as LDAP for identity management, SIEM for monitoring and logging, and HSM for encryption key management. This centralized approach ensures visibility, traceability, and auditability to meet regulatory requirements.
1. Data Protection at the Point of Ingestion
Sensitive data is protected immediately upon entering the corporate environment, whether sourced from applications, customer portals, or business systems. Application protectors integrated into middleware and streaming pipelines ensure that security policies are applied consistently, adhering to the “Data Protection by Design and Default” principle. This prevents unprotected data from propagating through the system.
2. Storage-Level Security
Sensitive data stored in SQL and NoSQL databases is encrypted at the column and row level, ensuring even privileged users cannot access unprotected data. This granular encryption aligns with compliance mandates that require strict controls over data at rest. Authorized decryption workflows retrieve and process the data securely while maintaining privacy.
3. Policy-Enforced Data Consumption
At the data virtualization layer, security policies managed by the ESA govern access to sensitive data. Queries from BI and reporting tools are evaluated against these policies, ensuring that data is decrypted only for authorized users. This enforces compliance with principles like least privilege and supports secure, controlled data access.
Navigate Compliance with Confidence
Frequently Asked Questions
01
How does Protegrity ensure compliance with global regulatory frameworks like the GDPR, HIPAA, and PCI DSS?
Protegrity’s platform applies centralized policies for encryption, tokenization, and access control, ensuring compliance with complex international regulations. By leveraging regional policy enforcement and real-time audit capabilities, organizations can confidently meet the GDPR, HIPAA, PCI DSS, and other regulatory requirements without compromising operational efficiency.
02
Can Protegrity adapt to evolving compliance regulations?
Yes, Protegrity’s flexible platform is built to adapt to new and changing regulations. The Enterprise Security Administrator (ESA) allows security teams to quickly update and deploy new policies globally, ensuring businesses stay ahead of compliance changes while minimizing disruptions.
03
How does Protegrity help organizations ensure audit readiness?
Protegrity automates compliance reporting and audit preparation by providing real-time logs, access monitoring, and built-in audit workflows. This ensures organizations can produce comprehensive reports for regulators efficiently, reducing manual overhead and the risk of non-compliance.
04
How does Protegrity protect sensitive data while maintaining compliance?
Protegrity secures sensitive data through vaultless tokenization, encryption, and role-based access controls. These measures ensure that data is protected throughout its lifecycle, meeting compliance requirements while enabling secure operations across hybrid and multi-cloud environments.
Take the next step
See how Protegrity’s fine grain data protection solutions can enable your data security, compliance, sharing, and analytics.
Get an online or custom live demo.