Tag: Data Privacy
-
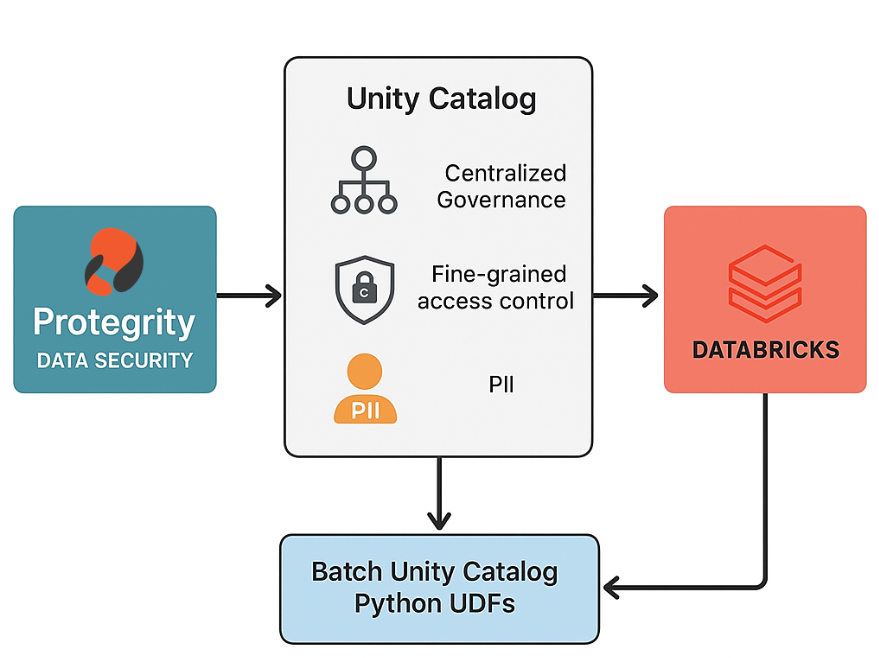
Can Your Current Architecture Handle Secure, High-Speed Analytics on Databricks?
As enterprises increasingly use Databricks for analytics and AI, protecting sensitive data on the platform is paramount. Protegrity’s data protection integration with Databricks ensures that even sensitive data (like PII) can be analyzed in the cloud safely and in compliance with regulations. Two recent advancements make this integration especially powerful: By combining Unity Catalog’s unified…
-
Balancing Data Privacy, Regulations and Revenue in Telecom
The need to find the balance between providing a unique and tailored customer experience, ensuring data privacy, and adhering to market regulations has become more critical than ever for Communications Service Providers (CSPs). In a world where customers are more demanding, regulations are more stringent, and attacks are more sophisticated, it’s easy to see how…
-
Privacy is Power: The Value of Training for Modern Data Protection
We’ve all seen it in the movies: The chief of security declares that no one could ever steal the “Famous Jewel” because it’s protected by thick glass, an impenetrable system of motion-detecting lasers, and, finally, a weight-sensitive sensor. Cut to the next scene, where a thief, dressed in sleek black, zip-lines from an open skylight,…
-
DATA TOKENIZATION EXPLAINED: 5 BASIC PRINCIPLES OF TOKENIZATION
WHAT IS DATA TOKENIZATION? Data tokenization protects sensitive data by substituting it with a randomly generated surrogate value known as a token. There are two types of data tokenization: vault and vaultless. Vault data tokenization stores information about tokenized data in a database, while vaultless generates tokens with algorithms to prevent easy access. Learn more…
-
2 DATA PROTECTION METHODS YOU NEED TO KNOW: ANONYMIZATION AND PSEUDONYMIZATION
WHAT IS ANONYMIZATION AND PSEUDONYMIZATION? ANONYMIZATION \ Ə-ˌNÄ-NƏ-MƏ-ˈZĀ-SHƏN PSEUDONYMIZATION \ SO͞ODƏNIMƏ-ˈZĀ-SHƏN Spelling, let alone pronouncing, “anonymization” and “pseudonymization” is just the beginning. Vocabulary, however, will be the least of the challenges for organizations that ignore the business value created through the use of these data protection methods. The amount of data keeps increasing, exponentially, and it moves quickly…
-
ONE CYBERSECURITY PLATFORM TO RULE THEM ALL: EXPLORING THE ONE ARCHITECTURE
Enterprises require multiple tools for cyber defense, so network and information security staff often end up managing a patchwork of solutions, a blend of legacy and new technologies. If they find and deploy solutions that solve several business and security problems at once, they can reduce costs, logistics, and headaches while helping the business grow…
-
CAN YOU UNLOCK DATA AND ELIMINATE THE RISK OF DATA LOSS?
Companies accumulate massive amounts of data, whether it is intellectual property or customer and employee information. Data is a critical asset: it’s undeniable. If your business users have appropriate access to data, they can perform their jobs more efficiently and effectively, and they can analyze the data to derive key business intelligence that drives better…